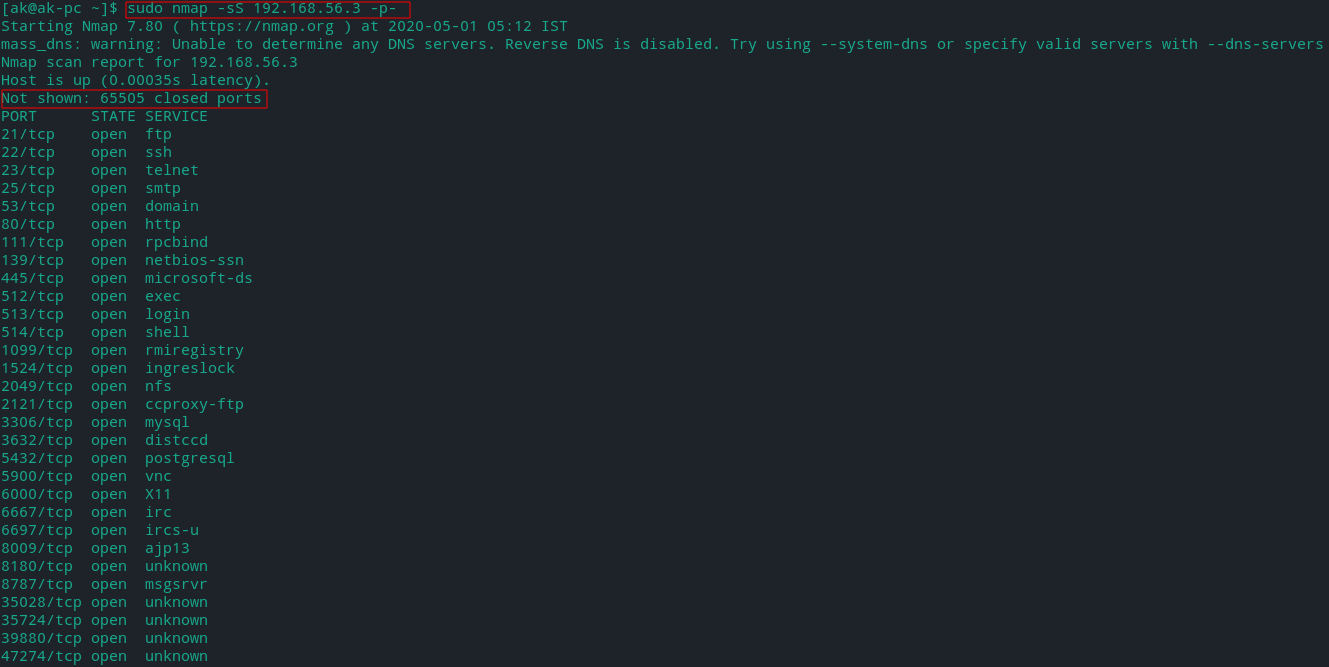
Scan all 65535 ports
By default Nmap only scan top 1000 ports and uses TCP as default protocol for port scan.
To scan all the 65535 ports we can use the -p 0-65535 or -p- option.
UDP Port Scan
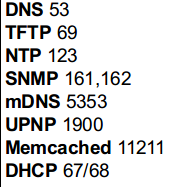
Most services on the internet uses TCP but services like DNS,SNMP and DHCP uses UDP.
UDP scan is slower and difficult as compare to TCP.
- Some common UDP services and ports:
How UDP scans work?
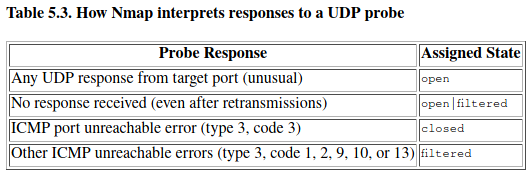
A UDP packet is sent to every targeted port.For ports such as 53 and 161, a protocol-specific payload is sent to increase response rate, but for most ports the packet is empty unless the --data, --data-string, or --data-length options are specified.
-
The most curious element of this table is the open|filtered state. Open ports rarely respond to empty probes.
-
Those ports for which Nmap has a protocol-specific payload are more likely to get a response and be marked open.
-
Version detection (-sV) can be used to help differentiate the truly open ports from the filtered ones.
-
Unfortunately, a Linux-style limit (linux rate limit ICMP port unreachable messages by default) of one packet per second makes a 65,536-port scan take more than 18 hours.
To speed up UDP scans:
- scan more hosts in parallel
- do a quick scan of just the popular ports first
- scan from behind the firewall
- use --host-timeout to skip slow hosts.
Scanning Metasploitable 2:
To scan all the UDP ports also we can use the -sU option (root privileges needed).
To scan both TCP and UDP ports we can use -sS (SYN scan) and -sU (UDP scan) options.
Use -T4 or -T5 to imporve speed and -sV or -sUV for service detection with UDP scan.
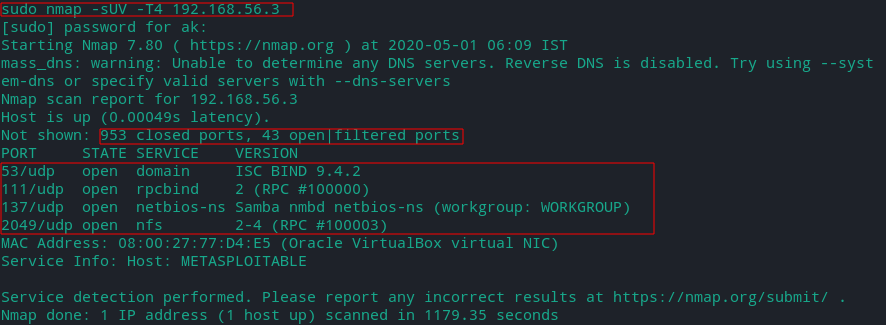

Scanning Top 10 UDP orts
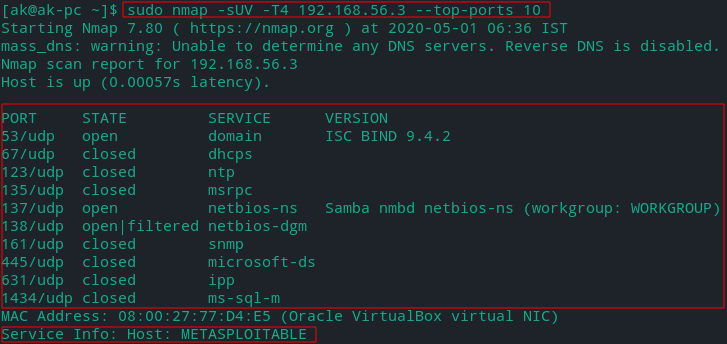
'--top-ports [number]' option can be used to scan most common ports which are usually open.
False Positives
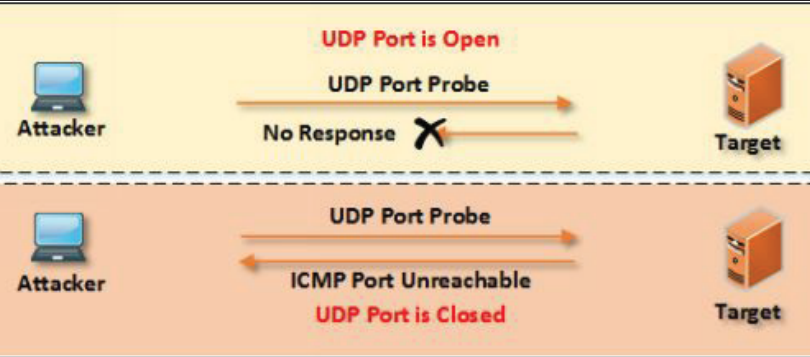
UDP scans may cause a lot of false positives. When a scanned UDP port is closed the system will respond with a ICMP port unreachable message. The absence of such packet indicates that the UDP port is open.
When a firewall is present on the target host which blocks the ICMP unreachable message than all UDP ports appear to be open.
All or Aggressive Scan
This scan is known as intense scan in zenmap. It's good to perform this scan first on a machine as it provides a lot of information.
Syntax:
For scanning all TCP ports
nmap -v -A -T4 -p- [TARGET]
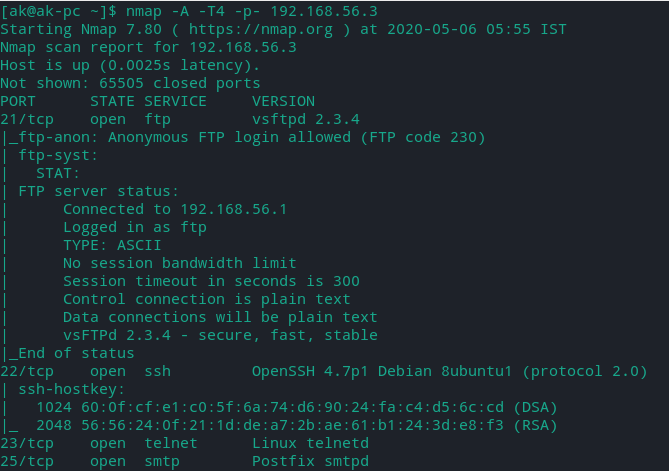
For Scanning top 1000 UDP ports
nmap -sU -v -A -T4 [TARGET]
Scans performed:
- OS detection (-O)
- version scanning (-sV)
- script scanning with default scripts (-sC)
- traceroute (--traceroute)
- timing (-T4)
- verbosity (-v)
Note:
-
Script scanning with the default set is intrusive.
-
OS detection and traceroute requires root.